CloudGuard Network security is used to set up native security for application workloads such as Oracle E-Business Suite or PeopleSoft ERP without significant configuration, integration, or business process changes.
Security in the cloud is based on a shared responsibility model. Oracle is responsible for the security of the underlying infrastructure, such as data center facilities, hardware, and software, to manage cloud operations and services. Customers are responsible for securing their workloads and configuring their services and applications securely to meet compliance obligations.
Oracle Cloud Infrastructure (OCI) offers best-in-class security technology and operational processes to secure its enterprise cloud services. Check Point CloudGuard Network Security for Oracle Cloud Infrastructure provides advanced, multilayered security to protect applications from attacks while enabling secure connectivity from enterprise and hybrid cloud networks. Together, they protect applications across on-premises data centers and cloud environments, delivering scalable performance and advancing security orchestration and unified threat protection.
Features of OCI
- Access controls (firewall)
- Logging
- Application control
- URL filtering
- Intrusion prevention (IPS)
- Advanced threat prevention (Anti-virus, anti-bot, SandBlast zero-day protection)
- Site-to-site virtual private network (VPN) for communication with the on-premises network
- Remote access VPN for communication with roaming users
- Network address translation for internet-bound traffic
Architecture of OCI
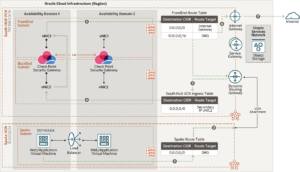
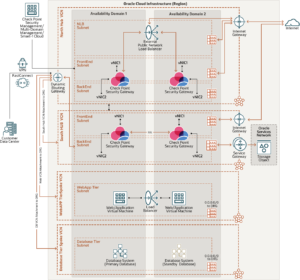
To protect traffic flows, Check Point recommends segmenting the network using a north and south hub and spoke design:
- The north hub protects publicly accessible resources from malicious inbound traffic. The north hub uses the Oracle flexible network load balancer that allows organizations to create a scalable set of CloudGuard Network Security gateways that can be sized appropriately based on throughput requirements.
- The south hub protects the traffic between spokes, traffic egressing to the internet, the Oracle Services Network, and traffic to or from on-premise networks. We recommend that the south hub contains a highly available cluster of CloudGuard Network Security gateways so that stateful failover can occur for traffic sensitive to interruption.
- Deploy each tier of your application in its virtual cloud network (VCN), which acts as a spoke. This separation allows for granular control of the traffic between spokes.
- The north hub VCN connects incoming traffic from the internet to the various spoke VCNs through a flexible network load balancer and dynamic routing gateway (DRG).
- The south hub VCN connects to the spoke VCNs through the DRG. All outgoing traffic and traffic between spokes use route table rules to route traffic through the DRG to the south hub for inspection by the CloudGuard Network Security cluster.
- Use one of the following methods to manage the environment:
- Centrally manage the environment with a Check Point Security management server or multidomain management server, deployed either in its subnet in the north hub VCN or as a pre-existing customer deployment accessible to the security gateways.
- Centrally manage the environment from Check Point Smart-1 Cloud management-as-a-service.
For each traffic flow scenario, ensure that network address translation (NAT) and security policies are configured on the CloudGuard Network Security gateways. The currently supported Flexible Network Load Balancer use case requires enabling source NAT on the firewalls from which traffic exits.
North-south inbound traffic flow through the north hub VCN
The following diagram illustrates how north-south inbound traffic accesses the web
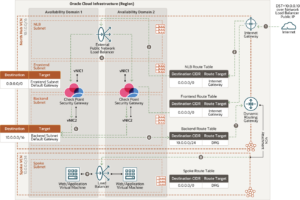
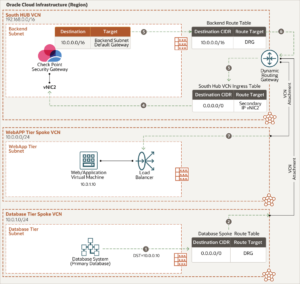
North-south outbound traffic flows through the south hub VCN
The following diagram illustrates how outgoing connections from the web application and database tiers to the internet provide software updates and access to external web services:
East-west traffic (web to database) flows through the south hub VCN
The following diagram illustrates traffic moving from the web application to the database tier.
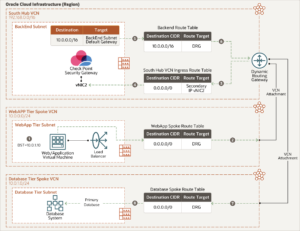
East-west traffic (database to web) flows through the south hub VCN
The following diagram illustrates traffic moving from the database tier to the web application.
East-west traffic (Web application to Oracle Services Network) flows through the south hub VCN
The following diagram illustrates how traffic moves from the web application to the Oracle Services Network.
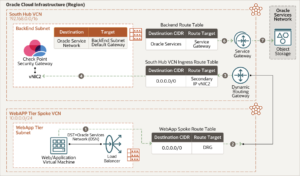
East-west traffic (Oracle Services Network to a web application) flows through the south hub VCN
The following diagram illustrates how traffic moves from the Oracle Services Network to the web application.
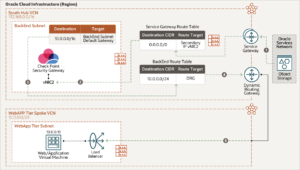
Architecture Components of OCI
- Check Point CloudGuard Network Security gateways.
- Check Point Security Management.
- Security management server
- Multidomain management
- Smart-1 Cloud management-as-a-service
- Oracle E-Business Suite or PeopleSoft application tier.
- Oracle E-Business Suite or PeopleSoft database tier.
- Region.
- Availability domain
- Fault domain
- Virtual cloud network (VCN) and subnet
- North hub VCN
- South hub VCN
- Application tier spoke VCN
- Database tier spoke VCN
- Load balancer
- Flexible Network Load balancer
- Security list
- Route table
- Internet gateway
- NAT gateway
- Dynamic routing gateway (DRG)
- Service gateway
- FastConnect OCI
- Virtual network interface card (VNIC)
- Private Ips
- Public Ips
- Source and destination check
Recommendations
VCN
When you create a VCN, determine the number of CIDR blocks required and the size of each block based on the number of resources you plan to attach to subnets in the VCN. Use CIDR blocks that are within the standard private IP address space.
Select CIDR blocks that don’t overlap with any other network (in Oracle Cloud Infrastructure, your on-premises data center, or another cloud provider) to which you intend to set up private connections.
After you create a VCN, you can change, add, and remove its CIDR blocks.
When you design the subnets, consider your traffic flow and security requirements. Attach all the resources within a specific tier or role to the same subnet, which can serve as a security boundary.
Use regional subnets and utilize the whole VCN CIDR as part of subnet CIDR, so all traffic from spoke VCNs gets inspected.
Check Point CloudGuard Network Security
- Deploy a high-availability cluster in the southern hub.
- Deploy a scalable set in the northern hub.
- Whenever possible, deploy in distinct fault domains or different availability domains at a minimum.
- Ensure that MTU is set to 9000 on all VNICs.
- Utilize SRIOV and VFIO interfaces (AMD shapes only).
- Create a second hub-spoke topology in a separate region for disaster recovery or geo-redundancy.
- Don’t restrict traffic through security lists or network security gateways (NSGs) because the security gateway secures all traffic.
- By default, ports 443 and 22 are open on the gateway, and more ports are open based on security policies.
Check Point Security Management
- If creating a deployment hosted in OCI, create a dedicated subnet for management.
- Deploy a secondary management server (high management availability) in a different availability domain or region.
- Use security lists or NSGs to restrict inbound access to ports 443, 22, and 19009 sourced from the internet to administer the security policy and view logs and events.
- Create a security list or NSG allowing ingress and egress traffic to the security gateways from the security management server.
Check Point security policies
Follow the latest security policies document on required ports and protocols.
Considerations
When securing Oracle E-Business Suite or PeopleSoft workloads on OCI using Check Point CloudGuard Network Security gateway, consider the following factors:
- Performance
- Selecting the proper instance size, determined by the Compute shape, determines the maximum available throughput, CPU, RAM, and number of interfaces.
- Organizations need to know what types of traffic traverse the environment, determine the appropriate risk levels, and apply proper security controls. Different combinations of enabled security controls impact performance.
- Consider adding dedicated interfaces for FastConnect or VPN services. Consider using large Compute shapes for higher throughput and access to more network interfaces.
- Run performance tests to validate that the design can sustain the required performance and throughput.
2. Security
-
- Deploying Check Point Security Management in OCI allows centralized security policy configuration and monitoring all physical and virtual Check Point Security gateway instances.
- For existing Check Point customers, migrating Security Management to OCI is also supported.
- Define distinct Identity and Access Management (IAM) dynamic groups or policies per cluster deployment.
3. Availability
-
- Deploy your architecture to distinct geographic regions for the greatest redundancy.
- Configure site-to-site VPNs with relevant organizational networks for redundant connectivity with on-premises networks.
4. Cost
-
- Check Point CloudGuard is available in bring-your-own-license (BYOL) and Pay As You Go (PAYG) license models for security management and security gateways in the Oracle Cloud Marketplace.
- Check Point CloudGuard Network Security gateway licensing is based on the number of vCPUs (one OCPU is equivalent to two vCPUs).
- Check Point BYOL licenses are portable between instances. For example, if you’re migrating workloads from other public clouds using BYOL licenses, you don’t need to purchase new licenses from Check Point. Check with your Check Point representative if you have questions or need verification of your license status.
- Check Point Security Management is licensed per managed security gateway. For example, two clusters count as four toward the Security Management license.
Deployment
There are two ways to deploy CloudGuard Network Security.
- You can Deploy by using the stack in Oracle Cloud Marketplace.
- Another way is to Deploy using the Terraform code in GitHub. You can customize it to suit your business requirement.
Now, you need an experienced IT System Integrator such as Tangenz, an Oracle Preferred Partner, if you need help with your application workloads on Oracle Cloud Infrastructure.
Connect with our OCI experts now!