Introduction
Private endpoint in Oracle Cloud Infrastructure (OCI) refers to a network setup for your Autonomous Database with shared Exadata infrastructure where all network traffic moves through a private endpoint within a VCN in your tenancy. If your organization has strict security mandates that do not allow you to have a public endpoint for your database, this provides you with the necessary private endpoint. Additionally, this configuration uses no public subnets and allows you to keep all traffic to and from your Autonomous Database off of the public internet.
Network prerequisites
- A VCN within the region that will contain your Autonomous Database with shared Exadata infrastructure. Cannot be changed after provisioning.
- A private subnet within your VCN configured with default DHCP options. Cannot be changed after provisioning.
- At least 1 network security group (NSG) within your VCN for the Autonomous Database. Can be changed or edited after provisioning.
Configuration Steps
You can create the VCN, subnet, and NSG and then configure the private endpoint when you provision or clone your Autonomous Database instance, or you can switch to using a private endpoint in an existing database that uses a public endpoint.
Configure Private Endpoints When You Provision or Clone an Autonomous Database Instance
These steps are applicable if you are provisioning or cloning an instance and you have completed the network prerequisite steps, and you are at the Choose network access step of the provisioning or cloning document.
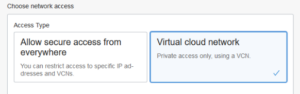
1. Select Virtual cloud network under Access Type section.
2. Select a Virtual cloud network in your compartment or if the VCN is in a different compartment click CHANGE COMPARTMENT and select the compartment that contains the VCN and then select a virtual cloud network.
![]()
3. Select the Subnet in your compartment to attach the Autonomous Database to or if the Subnet is in a different compartment click CHANGE COMPARTMENT and select the compartment that contains the Subnet and then select a subnet.
![]()
4. (Optional) Enter a Hostname prefix.
![]()
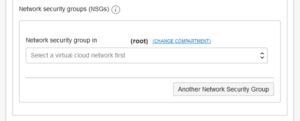
5. Select one or more Network security groups (NSGs).
To allow connections to the Autonomous Database instance, you need to define security rules in an NSG; this creates a virtual firewall for your Autonomous Database.
- A stateful ingress rule with the source set to the address range you want to allow to connect to your database, the IP Protocol set to TCP, and the Destination Port Range set to 1522.
- To use Oracle Application Express, Oracle SQL Developer Web, and Oracle REST Data Services, add port 443 to the NSG rule.
6. Complete the remaining provisioning or cloning steps as per respective documents.
Change from Public to Private Endpoints with Autonomous Database
If your Autonomous Database instance is configured to use a public endpoint you can change the configuration to a private endpoint.
Note: Changing an instance from a public to a private endpoint on Autonomous Database is only supported with Oracle Database 19c onwards.
1. On the Details page, from the More Actions drop-down list, select Update Network Access.
To change an instance from a public to a private endpoint, the Autonomous Database instance must be in the Available state (Lifecycle State: Available).
2. In the Update Network Access dialog, select Virtual cloud network.
3. Next follow the steps 2 to 5 from Configure Private Endpoints When You Provision or Clone an Instance.
4. Click Update and Confirm the changes.
Private Endpoints Configuration Examples on Autonomous Database
Connecting from Inside Oracle Cloud Infrastructure VCN
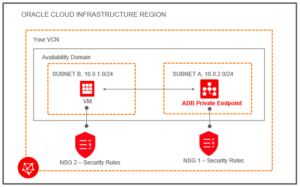
Below image shows an example VCN “Your VCN” in an Oracle Cloud Infrastructure region. This shows an Availability Domain containing two subnets: “SUBNET A” and “SUBNET B”. SUBNET B is the VM compute subnet. This has an associated security rule “NSG 2 – Security Rules”.
SUBNET A shows the Autonomous Database private endpoint, “ADB Private Endpoint”. This has an associated security rule, “NSG 1 Security Rules”. The Autonomous Database SUBNET A connects to the VM in SUBNET B.
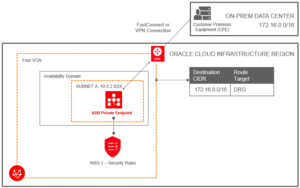
Connecting from Your Data Center to Autonomous Database
Below image shows a sample VCN with label “Your VCN”. This includes an availability domain with one subnet, “SUBNET A”. The subnet connects to the Autonomous Database with the label, “ADB Private Endpoint”. The subnet has an associated security rule, “NSG1 – Security Rules”.
The On-Prem Data Center connects to the Oracle Cloud Infrastructure region by FastConnect or VPN Connect. The Oracle Cloud Infrastructure region has a Dynamic Routing Gateway “DRG” defined between the On-Prem Data Center and the VCN.