Introduction
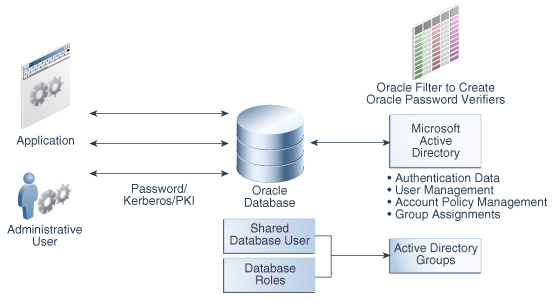
Starting with 18c, Oracle is providing a direct integration option for use cases where Microsoft Active Directory Users & Groups is needed for Authentication and Authorization. Database users & roles can map directly to AD users & groups without using Enterprise User Security (EUS). We can perform the integration either during the creation of Database or Post creation of Database.
In this article, I will list Basic requirements, Supported Authentication methods and High level integration steps.
Requirements
- Active Directory running on Windows 2008+.
- Oracle Database Enterprise Edition or higher version 18.1.0+ (Standard Edition is not supported).
- Kerberos version 5.
Supported Authentication methods
- Password Authentication
- Kerberos Authentication
- SSL Authentication
Integration Steps
- Integrate Oracle Database with Active Directory
- Configure Authentication
- Configure Authorization
Integrate Oracle Database with Active Directory
Step – 1: Create Service Account in Active Directory.
Step – 2: Create dsi.ora/ldap.ora file.
Step – 3: Request an AD Certificate for Secure connection.
Step – 4: Create a Wallet in Database server and import the AD certificate.
Step – 5: Configure Oracle Database – Active Directory connection.
Step – 6: Verify the Integration.
Configure Authentication
Use one of the following Authentication method from Supported Authentication methods.
Configure Password Authentication
Password Authentication allows Users to connect database using their Active Directory Username & Password. Below are high level to steps to configure it.
Step – 1: Install Password Filter and Extend AD.
Step – 2: Update database password file version to 12.2
Step – 3: Test the connection using AD account.
Configure Kerberos Authentication
Kerberos Authentication let users connect to the Database without entering their Username & Password, Instead it uses Windows logon credentials for Authentication. Use following steps to implement the design.
Step – 1: Install Kerberos v5.
Step – 2: Create Service Principal for Oracle Database Server.
Step – 3: Create Service Key table, Extract Key table from Kerberos and Copy it to Oracle Database Server.
Step – 4: Install Oracle client on Client machine.
Step – 5: Configure Kerberos Authentication on the Client, Database Server and update init & sqlnet parameters.
Step – 6: Create Kerberos User in Kerberos Server and Externally Authenticated User in Database Server.
Step – 7: Configure SQLNET on Oracle Client for Kerberos using Manual Ticket/Internal Credential Cache.
Step – 8: Test the connection to Database Server without username & password.
Configure SSL Authentication
SSL Authentication allows users to access Database using Server signed certificates, where Users are provided with SSL certificates rather than using Username – Password. Follow below steps to implement it.
Step – 1: Confirm wallet creation on the Database server performed during the Oracle Database – Active Directory integration.
Step – 2: Create Self Signed certificate for in the Database server wallet for Oracle Certification Authority.
Step – 3: Create and Configure wallet on the Client machine.
Step – 4: Create request certificate on Client machine, Export and Copy it to the Server wallet for signing it using Oracle CA created above.
Step – 5: Copy the signed certificate to Client machine and import into the wallet.
Step – 6: Create shared global user mapped with Active Directory User.
Step – 7: Specify the Certificate to use for Authentication in sqlnet.ora file on the Client machine.
Step – 8: Test the database connection.
Configure Authorization
There are 3 ways to provide Authorization to the Users connecting through AD.
- Mapping an AD Group to a Shared Database Global User.
- Mapping an AD Group to a Database Global Role.
- Mapping an AD User to Database Global User Exclusively.